Call us for a free evaluation on your current backup effectiveness. We can quote you on a cost-effective, custom backup solution for onsite and/or offsite backups to ensure your data is safe and secure!
Great News for MSU and the Golden Triangle!
Press Release – FAA Selects Mississippi State University Team As Center of Excellence for Unmanned Aircraft Systems
May 8, 2015
Contact: Laura Brown
Phone: 202-267-3883; Email: laura.j.brown@faa.gov
WASHINGTON – After a rigorous competition, the U.S. Department of Transportation’s Federal Aviation Administration (FAA) has selected a Mississippi State University team as the FAA’s Center of Excellence for Unmanned Aircraft Systems (COE UAS). The COE will focus on research, education and training in areas critical to safe and successful integration of UAS into the nation’s airspace.
The team brings together 15 of the nation’s leading UAS and aviation universities that have a proven commitment to UAS research and development and the necessary resources to provide the matching contribution to the government’s investment.
“This world-class, public-private partnership will help us focus on the challenges and opportunities of this cutting-edge technology,” said U.S. Transportation Secretary Anthony Foxx. “We expect this team will help us to educate and train a cadre of unmanned aircraft professionals well into the future.”
The COE research areas are expected to evolve over time, but initially will include: detect and avoid technology; low-altitude operations safety; control and communications; spectrum management; human factors; compatibility with air traffic control operations; and training and certification of UAS pilots and other crewmembers, in addition to other areas.
“This team has the capabilities and resources to quickly get up and running to help the FAA address the demands of this challenging technology over the next decade,” said FAA Administrator Michael Huerta.
The FAA expects the COE will be able to begin research by September 2015 and be fully operational and engaged in a robust research agenda by January 2016.
Congress appropriated $5 million for the five-year agreement with the COE, which will be matched one-for-one by the team members.
In addition to Mississippi State University, the other team members include: Drexel University; Embry Riddle Aeronautical University; Kansas State University; Kansas University; Montana State University; New Mexico State University; North Carolina State University; Oregon State University; University of Alabama, Huntsville; University of Alaska, Fairbanks; University of North Dakota; and Wichita State University.
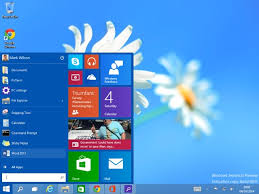
Windows 10 Technical Preview Available for viewing at our office!
If you have been curious about the look and feel of the upcoming Project Spartan (Windows 10) Operating System, be curious no more! We have a computer setup in our office that you are welcome to come by and take a look at! Our opinion??? There is a lot of work yet to be done before the final version is ready for release this summer, but overall, it appears that a lot of the complaints from the troubled Windows 8 have been heard by Microsoft! You are no longer forced to use the Metro Live Tile interface, the old, familiar desktop comes up as default. The new Start Menu gives us the best of both worlds, plus you can enlarge the menu to full screen view.
Biometric passwords give the ability to do face, finger, or iris scanning. Come take a look at the new task view button, virtual desktops (which we have seen on mac computers for years), increased performance (although it still won't run efficiently on older machines), web page annotation, and much more.
If you do have a touchscreen device, you will still get the full functionality that Windows 8 attempted to give you. For gamers, there are additional features such as an Xbox app that will be improved in the coming months.
"Windows 10 isn't going to fix everything, but these changes to Windows 8's most divisive elements have made a world of difference to the OS. And that's crucial to Windows' future, as Microsoft is still looking at the big picture: PCs are old news." ~cnet
Come on by... or call for an appointment, for us to give you a quick overview of the "new and improved" Windows 10.
Sign Up at irs.gov Before Crooks Do It For You!
If you’re an American and haven’t yet created an account at irs.gov, you may want to take care of that before tax fraudsters create an account in your name and steal your personal and tax data in the process. [USE LINK ABOVE TO GO TO IRS.GOV AND SELECT ONLINE TRANSCRIPT]
Recently, KrebsOnSecurity heard from Michael Kasper, a 35-year-old reader who tried to obtain a copy of his most recent tax transcript with the Internal Revenue Service(IRS). Kasper said he sought the transcript after trying to file his taxes through the desktop version of TurboTax, and being informed by TurboTax that the IRS had rejected the request because his return had already been filed.
Kasper said he phoned the IRS’s identity theft hotline (800-908-4490) and was told a direct deposit was being made that very same day for his tax refund — a request made with his Social Security number and address but to be deposited into a bank account that he didn’t recognize.
“Since I was alerting them that this transaction was fraudulent, their privacy rules prevented them from telling me any more information, such as the routing number and account number of that deposit,” Kasper said. “They basically admitted this was to protect the privacy of the criminal, not because they were going to investigate right away. In fact, they were very clear that the matter would not be investigated further until a fraud affidavit and accompanying documentation were processed by mail.”
In the following weeks, Kasper contacted the IRS, who told him they had no new information on his case. When he tried to get a transcript of the fraudulent return using the “Get Transcript” function on IRS.gov,
He learned that someone had already registered through the IRS’s site using his Social Security number and an unknown email address.
he learned that someone had already registered through the IRS’s site using his Social Security number and an unknown email address.
“When I called the IRS to fix this, and spent another hour on hold, they explained they could not tell me what the email address was due to privacy regulations,” Kasper recalled. “They also said they could not change the email address, all they could do was ban access to eServices for my account, which they did. It was something at least.”
FORM 4506
Undeterred, Kasper researched further and discovered that he could still obtain a copy of the fraudulent return by filling out the IRS Form 4506 (PDF) and paying a $50 processing fee. Several days later, the IRS mailed Kasper a photocopy of the fraudulent return filed in his name — complete with the bank routing and account number that received the $8,936 phony refund filed in his name.
“That’s right, $50 just for the right to see my own return,” Kasper said. “And once again the right hand does not know what the left hand is doing, because it cost me just $50 to get them to ignore their own privacy rules. The most interesting thing about this strange rule is that the IRS also refuses to look at the account data itself until it is fully investigated. Banks are required by law to report suspicious refund deposits, but the IRS does not even bother to contact banks to let them know a refund deposit was reported fraudulent, at least in the case of individual taxpayers who call, confirm their identity and report it, just like I did.”
Kasper said the transcript indicates the fraudsters filed his refund request using the IRS web site’s own free e-file website for those with incomes over $60,000. It also showed the routing number for First National Bank of Pennsylvania and the checking account number of the individual who got the deposit plus the date that they filed: January 31, 2015.
Kasper said he can’t prove it, buthe believes the scammers obtained that W2 data directly from the IRS itself, after creating an account at the IRS portal in his name (but using a different email address) and requesting his transcript.
The transcript suggests that the fraudsters who claimed his refund had done so by copying all of the data from his previous year’s W2, and by increasing the previous year’s amounts slightly. Kasper said he can’t prove it, but he believes the scammers obtained that W2 data directly from the IRS itself, after creating an account at the IRS portal in his name (but using a different email address) and requesting his transcript.
“The person who submitted it somehow accessed my tax return from the previous year 2013 in order to list my employer and salary from that year, 2013, then use it on the 2014 return, instead,” Kasper said. “In addition, they also submitted a corrected W-2 that increased the withholding amount by exactly $6,000 to increase their total refund due to $8,936.”
MONEY MULING
On Wednesday, March 18, 2015, Kasper contacted First National Bank of Pennsylvania whose routing number was listed in the phony tax refund request, and reached their head of account security. That person confirmed a direct deposit by the IRS for $8,936.00 was made on February 9, 2015 into an individual checking account specifying Kasper’s full name and SSN in the metadata with the deposit.
“She told me that she could also see transactions were made at one or more branches in the city of Williamsport, PA to disburse or withdraw those funds and that several purchases were made by debit card in the city of Williamsport as well, so that at this point a substantial portion of the funds were gone,” Kasper said. “She further told me that no one from the IRS had contacted her bank to raise any questions about this account, despite my fraud report filed February 9, 2015.”
The head of account security at the bank stated that she would be glad to cooperate with the Williamsport Police if they provided the required legal request to allow her to release the name, address, and account details. The bank officer offered Kasper her office phone number and cell phone to share with the cops. The First National employee also mentioned that the suspect lived in the city of Williamsport, PA, and that this individual seemed to still be using the account.
Kasper said the local police in his New York hometown hadn’t bothered to respond to his request for assistance, but that the lieutenant at the Williamsport police department who heard his story took pity on him and asked him to write an email about the incident to his captain, which Kasper said he sent later that morning.
Just two hours later, he received a call from an investigator who had been assigned to the case. The detective then interviewed the individual who held the account the same day and told Kasper that the bank’s fraud department was investigating and had asked the person to return the cash.
“My tax refund fraud case had gone from stuck in the mud to an open case, almost overnight,” Kasper sad. “Or at least it seemed to be that simple. It turned out to be much more complex.”
For starters, the woman who owned the bank account that received his phony refund — a student at a local Pennsylvania university — said she got the transfer after responding to a Craigslist ad for a moneymaking opportunity.
Kasper said the detective learned that money was deposited into her account, and that she sent the money out to locations in Nigeria via Western Union wire transfer, keeping some as a profit, and apparently never suspecting that she might be doing something illegal.
“She has so far provided a significant amount of information, and I’m inclined to believe her story,” Kasper said. “Who would be crazy enough to deposit a fraudulent tax refund in their own checking account, as opposed to an untraceable debit card they could get at a convenience store. At the same time, wouldn’t somebody who could pull this off also have an explanation like this ready?”
The woman in question, whose name is being withheld from this story, declined multiple requests to speak with KrebsOnSecurity, threatening to file harassment claims if I didn’t stop trying to contact her. Nevertheless, she appears to have been an unwitting — if not unwilling — money mule in a scam that seeks to recruit the unwary for moneymaking schemes.
ANALYSIS
The IRS’s process for verifying people requesting transcripts is vulnerable to exploitation by fraudsters because it relies on static identifiers and so-called “knowledge-based authentication” (KBA) — i.e., challenge questions that can be easily defeated with information widely available for sale in the cybercrime underground and/or with a small amount of searching online.
To obtain a copy of your most recent tax transcript, the IRS requires the following information: The applicant’s name, date of birth, Social Security number and filing status. After that data is successfully supplied, the IRS uses a service from credit bureau Equifaxthat asks four KBA questions. Anyone who succeeds in supplying the correct answers can see the applicant’s full tax transcript, including prior W2s, current W2s and more or less everything one would need to fraudulently file for a tax refund.
The KBA questions — which involve multiple choice, “out of wallet” questions such as previous address, loan amounts and dates — can be successfully enumerated with random guessing. But in practice it is far easier, said Nicholas Weaver, a researcher at theInternational Computer Science Institute (ICSI) and at the University of California, Berkeley.
“I did it twice, and the first time it was related to my current address, one old address question, and one ‘which credit card did you get’ question,” Weaver said. “The second time it was two questions related to my current address, and two related to a car loan I paid off in 2007.”
The second time round, Weaver said a few minutes on Zillow.com gave him all the answers he needed for the KBA questions. Spokeo solved the “old address” questions for him with 100% accuracy.
“Zillow with my address answered all four of them, if you just assume ‘moved when I bought the house’,” he said. “In fact, I NEEDED to use Zillow the second time around, because damned if I remember when my house was built. So with Zillow and Spokeo data, it isn’t even 1 in 256, it’s 1 in 4 the first time around and 1 in 16 the second, and you don’t need to guess blind either with a bit more Google searching.”
If any readers here doubt how easy it is to buy personal data on just about anyone, check out the story I wrote in December 2014, wherein I was able to find the name, address, Social Security number, previous address and phone number on all current members of the U.S. Senate Commerce Committee. This information is no longer secret (nor are the answers to KBA-based questions), and we are all made vulnerable to identity theft as long as institutions continue to rely on static information as authenticators. See my recent story on Apple Pay for another reminder of this fact.
Unfortunately, the IRS is not the only government agency whose reliance on static identifiers actually makes them complicit in facilitating identity theft against Americans. The same process described to obtain a tax transcript at irs.gov works to obtain a free credit report from annualcreditreport.com, a Web site mandated by Congress. In addition, Americans who have not already created an account at the Social Security Administration under their Social Security number are vulnerable to crooks hijacking SSA benefits now or in the future. For more on how crooks are siphoning Social Security benefits via government sites, check out this story.
Kasper said he’s grateful for the police report he was able to obtain from the the Pennsylvania authorities because it allows him to get a freeze on his credit file without paying the customary $5 fee in New York to place and thaw a freeze.
Credit freezes prevent would-be creditors from approving new lines of credit in your name — and indeed from even being able to view or “pull” your credit file — but a freeze will not necessarily block fraudsters from filing phony tax returns in your name.
Unless, of course, the scammers in question are counting on obtaining your tax transcripts through the IRS’s own Web site. According to the IRS, people with a credit freeze on their file must lift the freeze (with Equifax, at least) before the agency is able to continue with the KBA questions as part of its verification process.
This entry was posted on Monday, March 30th, 2015 at 12:23 am and is filed under A Little Sunshine, The Coming Storm, Web Fraud 2.0.
Things To Know About The Firing Of Chancellor Dan Jones
Medical Mergers Bring HIPAA Breaches
Hospitals and medical groups are in a frenzy of mergers and acquisitions, but many are not protecting themselves from the increased risk of HIPAA breaches that results. The latest example comes from Northwestern Medical Group, a highly respected healthcare organization based in Chicago. On December 19th, Northwestern announced that an employee laptop with nearly 3,000 medical records was stolen from a vehicle, as reported by the Chicago Tribune. HIPAA also requires Northwestern to post a conspicuous notice of the breach on its website.
Unfortunately, theft is no excuse when it comes to protecting patient information, so the loss of the laptop is a major HIPAA violation. As with all breaches of 500 or more patient records, Northwestern must inform all affected patients by letter, provide notice to the media, and report the breach to HHS.
The organization will almost certainly face a large fine from the federal government for failing to protect patient information. Northwestern may also face lawsuits, and most organizations that suffer major breaches provide free credit monitoring to affected patients, which is an additional expense.
Finally, there is the intangible cost of the damage to Northwestern’s reputation. HIPAA violations disprove the old adage that there is no such thing as bad publicity.
Mergers play into this story because the employee actually worked for Northwestern Lake Forest Hospital, which Northwestern acquired in 2010. Northwestern has stated that the laptop was password-protected but unencrypted. Thus, the organization was in violation of the HIPAA Security Rule provision that Protected Health Information (PHI) should be protected by encryption.
Password protection does not satisfy the requirement, because password protection is easy to circumvent and the data can still be read. However, if the PHI had been encrypted, the theft of the laptop would not have constituted a breach, and Northwestern would have been spared the embarrassment and considerable expense of this incident. The government reports that 60 percent of all HIPAA breaches could have been prevented by encryption.
Northwestern states that it has “a robust privacy and security program, including encryption of laptop computers.” However, it is evident that this same compliance program was not properly implemented at Lake Forest Hospital. If it had been, the employee would never have loaded unencrypted PHI onto an easily stolen laptop. The employee should have been trained on the grave risk posed by failing to adequately protect patient data.
In my work with providers who are engaged in mergers, compliance is often an afterthought, if it is ever considered at all. These providers do not seem to appreciate that every institution has its own compliance strengths and weaknesses. While the core institution may have a robust HIPAA compliance program, the acquired organization may well have a much weaker program. Yet, these weaker programs are often left in place, even though it exposes the entire organization to risk.
The problem is often worse when hospitals acquire ambulatory practices, because the latter have typically lagged behind hospitals in implementing robust compliance programs. These practices are ticking time bombs for a major HIPAA violation, and it is the hospital or medical group that will suffer the financial and media repercussions.
Another element of this story deserves comment. The theft occurred on October 21st, 2014. However, Northwestern did not publicize the breach until December 19th. HIPAA requires providers to inform affected patients and HHS of a breach within 60 days. But in its notice, Northwestern states that it only “began” sending letters to affected patients on December 19th. It states that all patients should receive notice by January 9th, 2015. However, any notification to patients delivered later than December 21st constitutes another HIPAA violation, which may result in even heavier fines on the organization.
Apart from the law, it is hard to imagine why Northwestern waited so long to inform patients. Northwestern reports that the laptop “may have contained patients’ names, addresses, dates of birth, health insurance information, billing codes, date of services, physician’s name, medical record numbers, diagnosis, treatment information, and, in some limited instances, Social Security numbers.” This data provides a bonanza for identity theft. Surely, the affected patients should not have had to wait 60 days or more to learn that this information had been exposed.
Healthcare mergers make sense for a variety of reasons, including improved efficiency, better interoperability, stronger finances, and even improved patient care. But HIPAA compliance and digital security must not be neglected in the process. Northwestern recently concluded an even larger merger with Cadence Health. Let us hope that Northwestern is taking aggressive action to ensure that robust compliance programs are in place across every part of the organization.
2015 | By Brian Johnson - 4medapproved.com